IASME Cyber Assured.
The first step for UK organisations wanting to prove their dedication to data security.
What is IASME Cyber Assured?

Level 1
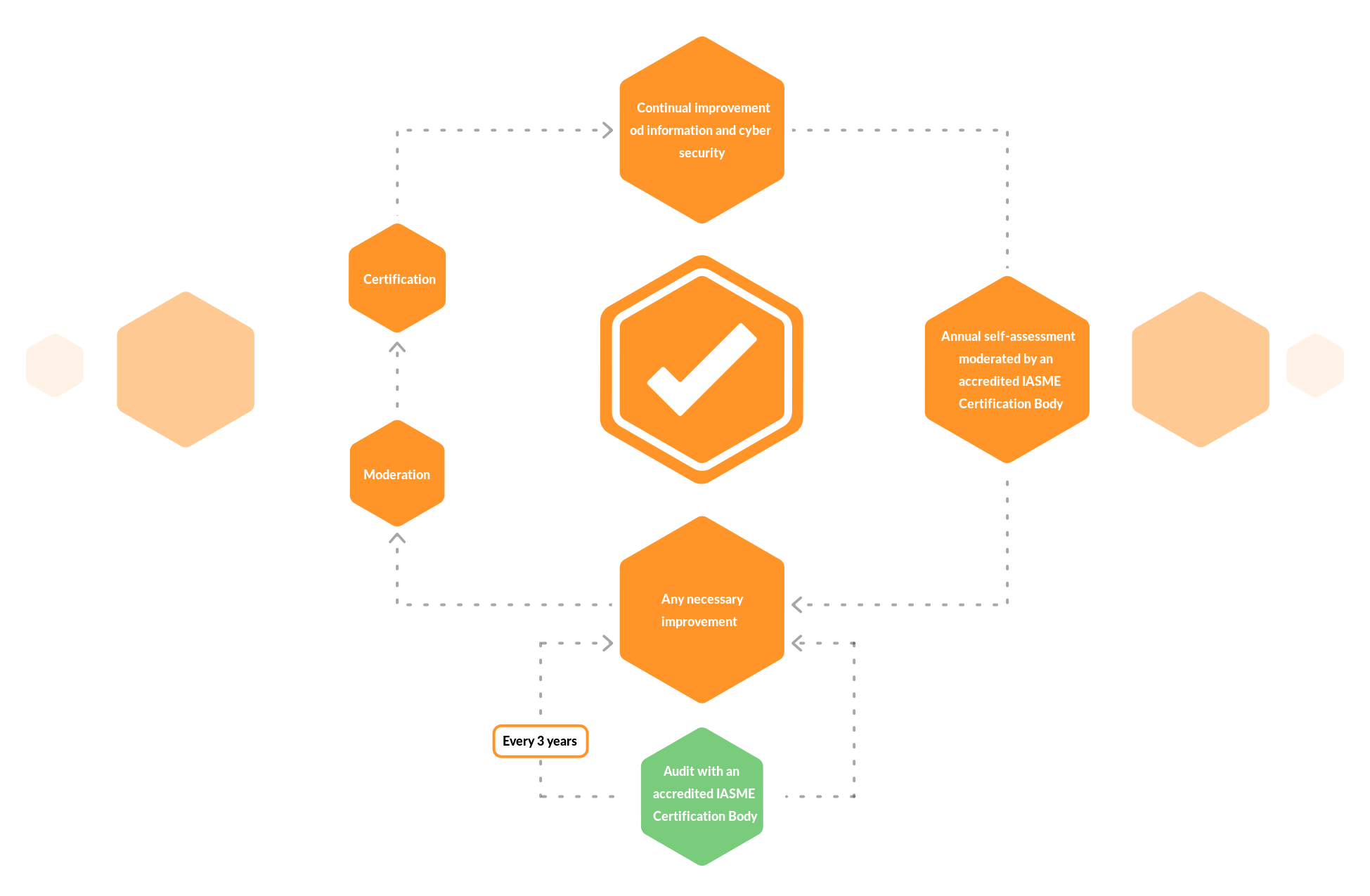
IASME Cyber Assured Level 1 is a Self-Assessment Questionnaire that is reviewed by an auditor who will issue either a pass or fail. Level 1 ensures that you have a base level of information security assurance around the 13 key themes IASME has identified to help bolster the level of information security for organisations. This certificate remains valid for 1 year, and will require renewal each year.
Level 2
IASME Cyber Assured Level 2 is a continuation from Level 1, however to achieve Level 2 a thorough audit will be conducted by a qualified auditor. The auditor will review documentation, interview key staff and observe processes that may support the ISMS. An audit report will be created by the auditor which will then be ratified by IASME’s moderators whereby either a pass/fail award will be issued.
The level of certification remains valid to up to 3 years, however to maintain this certificate level 1 must be achieved annually.
Level 2 Certification
Theme 1
Planning
Planning of information security is required to meet the standard. It’s important to include security considerations when planning to mitigate incidents tuning into very expensive surprises.
Theme 2
Organisation
The organisation theme aims to ensure an appropriate structure is in place within an organisation whereby roles and responsibilities are set. This theme also takes into consideration information resources to which your organisation may have access to, such as that through a supply chain.
Theme 3
Assets
Understanding where all your information assets are and how they fit together within your organisation is essential. This section also covers physical devices that may store or have access to your data. Knowing which assets are critical, and whom has responsibility for such assets is paramount when implementing a functioning ISMS.
Theme 4
Legal and regulatory landscape
To meet the IASME Cyber Assurance standard, every organisation must be aware of their legal and regulatory landscape. Legally enforceable obligations are associated with every organisation such as data handling and accounting to name a few. Some obligations may be more specific, such as the PCI-DSS standard required for organisations that handle payment card data.
Theme 5
Assessing and treating risks
An organisation must understand its risks and treat those risks appropriately. Carrying out a risk assessment and treating any risks following your organisation’s risk appetite can help improve your ISMS. Organisational risks take into consideration a broad range of areas in addition to informational security risks such as: Market risk, political risk, environmental risk and health and safety risks, to name a few.
Theme 6
Physical and environmental protection
Physical and environmental protection must also be considered when thinking about implementing a functioning ISMS. This can include physical protection considerations for assets such as locked cabinets for secure servers, or even having sufficient insurance to mitigate a financial impact from a natural disaster such as flooding.
Theme 7
People
People are integral to almost every organisation that exists and are a key consideration for any organisation. People are generally representatives of the organisations they work for, so when given access to sensitive corporate data people must be trained to handle data appropriately.
Theme 8
Policy
Company policies specify the guidelines, rules, and regulations that you require people in your organisation to follow. To aid a functioning ISMS, information security considerations must be established within company policies. Active policies must be reviewed to ensure they stay relevant and approved by appropriate personnel internally. Company policies must also be readily available for employees, as policies can help guide employees through certain processes such as an Incident Management Policy.
Theme 9
Managing Access
Managing access takes into consideration both digital and physical access. This theme encourages users to be granted access to resources and data that are solely necessary to their roles. Often an RBAC (Role Based Access Control) system is implemented to facilitate access management.
Theme 10
Technical Intrusion
The technical intrusion theme sets out a baseline of security measures to ensure your organisation is resilient against cyber-attacks. You are expected to have functioning anti-malware software deployed along with recurring vulnerability scanning to meet the standard. Where appropriate or deemed necessary by your risk register, penetration testing may support compliance with this theme.
Theme 11
Backup and restore
Theme 11 looks into the backing up and restoration of data and systems. Key things considered in theme 11 are around the frequency of backups as well as completing restoration tests to ensure backups are functioning.
Theme 12
Secure Business Operations
Secure Business Operations considers day-to-day organisational activities as well as regular monitoring of systems. Ensuring operations are smooth, anomalies may be identified via the monitoring process to highlight flaws in an ISMS or even point to an indicator of compromise. Setting internal objectives can help track an organisation’s growth and help identify any weaknesses.

Theme 13
Resilience: Business Continuity, incident management and disaster recovery Resilience for organisations has proven critical for many organisations over the years, however without proper planning, many organisations may have failed. Business continuity and disaster recovery highlight a chain of command and support processes to ensure an organisation may continue to operate during difficult times. To activate a business continuity plan often requires the permission of an executive level of staff, leading up to that, incident management handling may be crucial to make an informed decision.
Why choose Omni?
OmniCyber Security is an IASME consortium-appointed independent auditor and an accredited Cyber Essentials certification body. OmniCyber Security has the skilled knowledge to help you meet the standards set out in IASME and the Cyber Essentials Scheme. We also offer consultation services to businesses that wish to implement ISO27001.
Cost effective security
IASME is the most cost-effective way to raise security defences and meet government standards for IT security. For small companies, IASME accreditation is seen as the best route to achieve satisfactory cybersecurity defences.
Independent auditors
OmniCyber Security has been appointed as an independent auditor by the IASME Consortium for the IASME standard for those companies that wish to demonstrate a higher level of commitment to cybersecurity, rather than following the self-assessment route. IASME is a realistic and affordable way for SMEs to prove that they are following best security practices.
Why get accredited?
IASME, at a realistic cost, allows SMEs in a supply chain to demonstrate their level of cybersecurity and that they can properly protect their own and their customers’ information. Achieving IASME certification can also form a strong foundation for companies wishing to undergo certification to ISO27001 as part of a longer-term security strategy.
Why Omni
We use industry certified techniques and tools to help clients rapidly identify and rectify security gaps everywhere their people, products and customers interact with technology.
Some of the biggest brand globally trust our highly qualified and experienced team to ensure their systems and infrastructure are secure and compliant.
Whilst our teams can be relied upon to provide excellence in a single engagement, Omni excel at helping our clients mitigate the risks of their changing threat landscape for the long term, through a bespoke delivery of compliance and security services.
PEN TESTING
Find out where you are vulnerable, before hackers do
Sometimes offence is the best defence against cyber criminals. That’s why we provide a detailed mix of IT security services like CREST certified penetration testing, social engineering, web application testing and more. We search for the security gaps and give you the streamlined recommendations you need to fill them fast.
MANAGED SECURITY
Prevention is the best medicine
The average cost of a data breach in 2019 came at the bargain price of US$3.92 million. Large enterprises have the resources to absorb a hit like this, but most businesses don’t. This is where Managed Security comes in. As your embedded cybersecurity team, we provide network monitoring and advanced threat detection to minimise your risk of business disruption.
COMPLIANCE
Safeguard data, protect your customers and yourself
Do you get butterflies when you hear the words GDPR, PCI DSS, IASME, PIPEDA, CCPA? Getting Compliance right is a big deal and gets more complicated day-by-day. We can help. Our Compliance team has all the knowledge and tools you need to integrate best practices for data privacy across your entire organization and keep you resilient in face of a data breach.

