Firewall Configuration.
Don’t let poor firewall configuration bring your business down. Protect your data with a strong defence.
Get a free quote by filling out the form.
What is firewall configuration?
Firewalls are network security devices (software or hardware) that are essentially a barrier that sits between your devices and the internet, or other external sources of data. Firewalls form an essential part of any company’s cybersecurity architecture, overseeing the safety of outgoing and incoming network traffic.
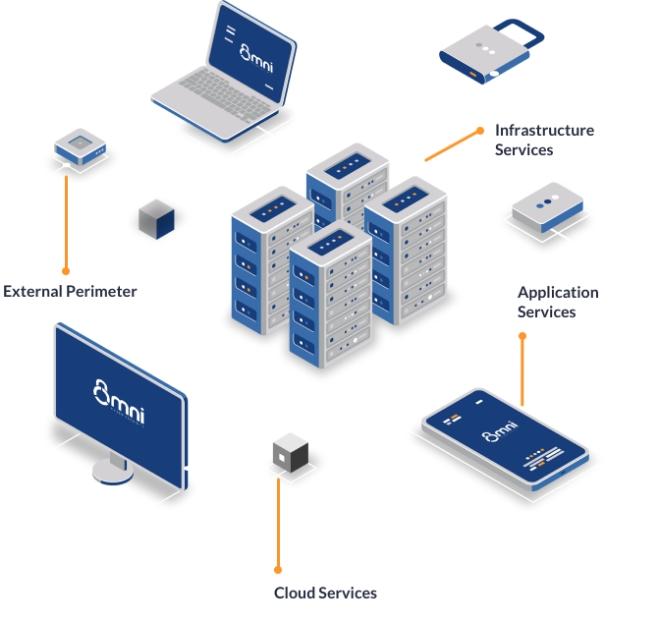
Firewall configuration services
-
Packet Filtering Firewalls
Packet-filtering firewalls are the most common type of firewall, although they only offer very limited protection against cyber-attacks and unauthorised access. Packet filtering firewalls examine each packet of incoming data and only allow them through if they match an established security rule.
-
Proxy Firewalls
Proxy firewalls or application firewalls assess and filter traffic at the application level. A proxy firewall is an intermediary firewall that sits between two end systems. The firewall will evaluate the packet and then it will either be blocked or permitted. This function is known as deep packet inspection (DPI) or Layer 7 inspection and it looks at the data within the packet, as opposed to just the header or name of the packet.
-
Next-generation Firewalls
Next-generation firewalls (NGFW) have additional technology called deep packet inspection, that proxy firewalls and packet-filtering firewalls do not have. Next-generation firewalls can perform encrypted traffic inspection, anti-virus functions, and include intrusion prevention systems.
-
Network Address Translation Firewalls
These work to keep individual IP addresses hidden, so that attackers can not capture specific or individual details, that can be used to attack individual IP addresses. Network address translation firewalls are similar to proxy firewalls but act as a barrier between outside traffic and a set of computers or devices within a network.
-
Stateful Multilayer Inspection Firewalls
These firewalls compare packets against known trusted packets at the network, application, and transport layers. Stateful multilayer inspection firewalls examine the whole packet and then pass each layer individually. They can determine the state of the communication to make sure that communications can only occur with trusted sources.
How do firewalls work?
Firewalls work by assessing the incoming traffic based upon a predetermined set of rules.
The firewall filters traffic from suspicious or unsecured sources, and this sits at the traffic entry point of a computer or laptop. These entry points are known as ports. It is at the ports where data from external devices is exchanged.
Why have a firewall?
A firewall is an integral part of an organisation’s cybersecurity strategy. When combined with other security measures, it can be highly effective.
Your firewall can have its own distinct set of rules for outgoing and incoming server traffic. Outgoing rules are equally important to incoming rules. This is because if the server has been compromised by a cybercriminal, then the outgoing firewall rules can stop unwanted outgoing communication.
Internal & Perimeter Firewalls.
Firewall best practices
Firewall configuration best practices include using internal firewalls in addition to your perimeter firewall. Your perimeter firewall only protects your systems from external attacks or malicious activity.
Internal firewalls offer a degree of protection against insider attacks and protect individual assets in the network if another asset is compromised. This makes it much harder for an attacker to move from one system to another and this gives you more time to respond to an attack.
Needs Regular Analysis.
Keep on top
You should employ a cybersecurity management company that will check for regular security updates to firewall software. Just like any other software, firewall software can have vulnerabilities. The firewall software creators will provide updates, called patches, to remove these vulnerabilities as they are discovered.
Why Omni
We use industry certified techniques and tools to help clients rapidly identify and rectify security gaps everywhere their people, products and customers interact with technology.
Some of the biggest brand globally trust our highly qualified and experienced team to ensure their systems and infrastructure are secure and compliant.
Whilst our teams can be relied upon to provide excellence in a single engagement, Omni excel at helping our clients mitigate the risks of their changing threat landscape for the long term, through a bespoke delivery of compliance and security services.
PEN TESTING
Find out where you are vulnerable, before hackers do
Sometimes offence is the best defence against cyber criminals. That’s why we provide a detailed mix of IT security services like CREST certified penetration testing, social engineering, web application testing and more. We search for the security gaps and give you the streamlined recommendations you need to fill them fast.
MANAGED SECURITY
Prevention is the best medicine
The average cost of a data breach in 2019 came at the bargain price of US$3.92 million. Large enterprises have the resources to absorb a hit like this, but most businesses don’t. This is where Managed Security comes in. As your embedded cybersecurity team, we provide network monitoring and advanced threat detection to minimise your risk of business disruption.
COMPLIANCE
Safeguard data, protect your customers and yourself
Do you get butterflies when you hear the words GDPR, PCI DSS, IASME, PIPEDA, CCPA? Getting Compliance right is a big deal and gets more complicated day-by-day. We can help. Our Compliance team has all the knowledge and tools you need to integrate best practices for data privacy across your entire organization and keep you resilient in face of a data breach.

