Is it possible for a cyber attacker to go from no access at all to Domain Admin? (Spoiler: yes, it is) On the whole, your network may appear secure, but hidden vulnerabilities strung together can give bad actors a path to control over your organisation. In this case study, we dissect a recent penetration test where our team at OmniCyber Security did just that. By identifying and exploiting multiple vulnerabilities, they created a cyber kill chain that compromised a client’s network from the ground up.
What is a Cyber Kill Chain?
The phrase “kill chain” can refer to different things in cyber security. It’s often used to describe the broad steps an attacker takes to achieve their objective, from the initial breach to the final goal, such as data exfiltration or system control. Those steps are:
- Reconnaissance
Intruder picks a target, researches it, and looks for vulnerabilities. - Weaponisation
Intruder develops malware designed to exploit the vulnerability. - Delivery
Intruder transmits the malware through a medium such as phishing. - Exploitation
The malware begins executing on the target system. - Installation
The malware installs a backdoor or other ingress accessible to the attacker. - Command and Control
The intruder gains persistent access to the victim’s systems/network. - Actions on Objective
Intruder initiates end goal actions, such as data theft, corruption, or destruction.
Originally developed by Lockheed Martin, some argue that this cyber kill chain model has become outdated in the constantly changing threat landscape.
In this case study, “kill chain” refers to our team of consultants stringing together a series of vulnerabilities as part of a penetration test to ascend through a client’s network from an unauthenticated user to Domain Administrator. This attack sequence replicates the tactics used by modern cyber criminals to give our clients an accurate picture of how their people and defences would stand up against a cyber attack.
Case Study
In this engagement, our client was an educational institution with a large network of thousands of users comprising staff and students. An organisation this size has many challenges, some of which became clear in the engagement. Separately from the kill chain, our team found outdated software with known vulnerabilities published online that could be exploited by any bad actor.
The most crucial part of the engagement involved chaining multiple vulnerabilities, which allowed OmniCyber Security to execute a kill chain, progressing from an unauthenticated position on the network to Domain Administrator.
The initial access point was a Network File System (NFS) Share that exported the home directory of a Linux machine on the network. This share was configured in a way that allowed OmniCyber Security to mount it as the root user. During enumeration, the team discovered that most users had Secure Shell (SSH) keys in use, and a setup script in the ansibot user’s home folder indicated this user had sudo rights with no password required.
OmniCyber Security used the root read/write access provided by the NFS Share misconfiguration to add their own SSH public key to the authorized_hosts file, allowing them to connect via SSH as the ansibot user. The first step in the kill chain was complete.
After establishing an SSH connection as ansibot, the consultant used the sudo -s command to escalate privileges to the root user, enabling the subsequent steps in the chain.
As the root user on the Linux machine, the consultant spent some time finding ways to pivot into the Active Directory environment. The machine was domain-joined, allowing OmniCyber Security to access System Security Services Daemon (SSSD) cached files related to Kerberos authentication. This was only possible thanks to the previous step, as they are only accessible as the root user. This allowed the team to retrieve approximately 99,000 potential domain objects.
Using the list of domain objects, the consultant sprayed them against a Domain Controller, resulting in over 38,000 valid usernames. The client’s weak password policy created the next weak link in the kill chain, as OmniCyber Security then conducted a password spraying attack, eventually gaining access.
While the policy in place in the domain had a minimum character length of 14, many passwords found during later password cracking did not meet this requirement, because the passwords never expired and therefore were never subject to the new rules. This meant that any passwords set before the current policy remained valid within Active Directory.
For reference, this is how much of a difference a strong password policy can have on brute force attacks:
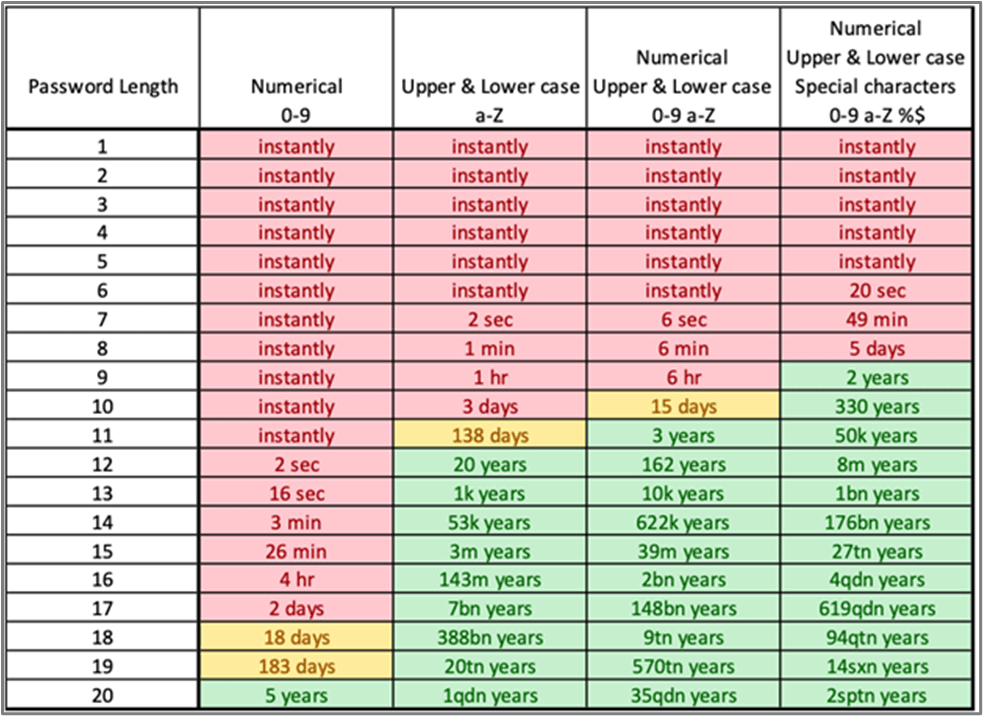
It’s important to note that the figure above represents the time it would take to ‘brute-force’ passwords of these lengths from retrieved password hashes. Using wordlists can significantly speed up this process by targeting predictable formats and words. Humans are not good at creating or remembering random strings. Therefore, OmniCyber Security recommends requiring users to have a strong password for logging into their workstations and then using a password manager for other application passwords. The password manager will also decrease the chances of reusing passwords in the environment.
A strong password policy would be:
Minimum of 10 characters (ideally 14+),
At least one of each of the following character sets:
- Lowercase alpha [a-z]
- Uppercase alpha [A-Z]
- Number [0-9]
- Symbol [!”£$%^&*(),./?[]{};’#:@~<>]
- Rotation of passwords every 90 days
- No repetition of passwords within 3 rotations
As many of the passwords in the domain were from before the updated password policy, it was possible to gain access to Active Directory as a user with a very weak guessable password.
After authenticating to the domain, OmniCyber Security performed Lightweight Directory Access Protocol (LDAP) queries on the domain controllers to gather information related to users, groups, roles, privileges, and sessions. This process led to the discovery of a significant vulnerability (ESC1) in Active Directory Certificate Services (AD CS), which allowed any user to impersonate others, including Domain Admins, and escalate their privileges to that group.
The consultant exploited the AD CS vulnerability to request a .pfx file for a user in the Administrators group. Typically, the team would use Kerberos to request the hash for the krbtgt account, the “golden ticket” of an Active Directory network. However, due to the network’s configuration, in this case, they used the more limited “Pass The Cert” technique, employing LDAP commands to add a user account to the domain and assign it to the Domain Admins group.
With a Domain Admin account, OmniCyber Security demonstrated their capabilities by executing a DCSync attack, allowing them to obtain all user NT hashes, which was a fitting conclusion to the engagement. In a real cyber attack scenario, a malicious actor could use these hashes for authentication or attempt to crack them to reveal plaintext passwords. Moreover, the actor could leverage the Domain Admin position to carry out various malicious actions, including encrypting files, wiping data, or exfiltrating data.
Recommendations to Client
- NFS Share Security: Do not make NFS Shares world-readable.
- Password Policies: Implement a stronger password policy and enforce it by requiring users to change their passwords to comply.
- Active Directory Security: Regularly review and secure AD CS configurations.
This case study highlights the importance of a comprehensive and meticulous approach to cyber security. By combining several vulnerabilities, our consultants were able to build their way up to Domain Admin access step by step. Organisations can significantly reduce the risk of a successful attack by understanding cyber kill chains and identifying the combined risk of potential vulnerabilities in their network.
For more information on how to secure your network and prevent similar attacks, contact OmniCyber Security today. Our expert team is ready to help you strengthen your cybersecurity posture and protect your critical assets.

